
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
What is hardware concurrent fingerprint? BitBrowser Fingerprint Browser Detailed Explanation
Time: 2024-07-27 10:53 Click:

When you browse social networking sites such as Facebook and Instagram, or e-commerce sites such as Amazon and Etsy, these sites will unknowingly collect many details about your browser: such as your IP address, the operating system you use (such as Windows or macOS), the screen resolution of your device, and even the specific fonts you have installed. These seemingly insignificant information, once gathered together, constitute a browser fingerprint. This fingerprint is unique in most cases, just like a fingerprint in the real world, which allows the website to identify you as a unique visitor.
For example, when you visit an e-commerce website, it collects your above information. When you visit again next time, even if you are not logged in, the website can quickly identify you with this unique browser fingerprint. For example, when you browse a social networking site, even if you change your username or some other common identifiers, this browser fingerprint can still allow the website to determine that it is you who is visiting. This unique identification method is quietly carried out without your knowledge, which poses a potential risk to your privacy. This article will provide you with a detailed explanation of hardware concurrent fingerprints and learn how to prevent the risk of associated account suspension caused by hardware concurrent fingerprints.

1. In-depth analysis of hardware resource concurrency identification
1.1 Exploring the mystery of HardwareConcurrency
In the vast world of browsers, HardwareConcurrency is like a silent hero behind the scenes. It is a member of the NavigatorAPI, seemingly low-key, but contains huge energy. Its task is to report to the outside world the number of processor cores that the browser can use to execute JavaScript code. Imagine that this information is like a password inside the device. Once obtained by criminals, it may become an important clue for them to track user behavior.
For example, suppose you are browsing a seemingly ordinary shopping website, and the website obtains the HardwareConcurrency information of your device and learns that your device has powerful processing power. It may infer that you are a user with high consumption power for high-end electronic products. Then, you may find that the page keeps pushing high-priced electronic product advertisements, which is undoubtedly an infringement of your privacy.
1.2 The two sides of concurrent identification of hardware resources
Concurrent identification of hardware resources actually analyzes the unique configuration of hardware components such as the CPU and GPU of the device to draw a unique "digital fingerprint" for each device. This technology is like a double-edged sword. On the one hand, it has significant potential in improving user experience and optimizing website performance. For example, some online game platforms can adjust the game quality and fluency according to the hardware configuration of the player's device to provide a better gaming experience.
However, on the other hand, it also opens a dangerous door to privacy leakage. Websites and service providers may use the information obtained by concurrent identification of these hardware resources to accurately profile users. They can not only understand your interests and consumption habits, but also infer the nature of your work and lifestyle. Although this accurate user portrait seems attractive in commercial marketing, it seriously infringes on the privacy rights of users.
Take social media platforms as an example. They may judge your online habits and active time based on the hardware characteristics of your device, so as to push targeted advertisements when you are most likely to be online. This not only makes you feel monitored, but also may cause you to receive a lot of unnecessary information interference.

2. Strategies for building a privacy protection network
2.1 Clearly understand the dual impact of concurrent identification of hardware resources
Like a double-edged sword, concurrent identification of hardware resources not only provides advertisers with precise delivery tools, but also poses a huge threat to the privacy and security of users. Every interest point, every expression of preference, and even every purchase behavior of users may be deeply analyzed and used through this technology. Therefore, enhancing one's own privacy awareness and fully understanding the potential risks that this technology may bring are the key first steps in protecting personal privacy.
2.2 Practical defense: building a multi-level privacy protection system
First, it is crucial to choose a privacy-enhanced browser. Such browsers usually have powerful built-in privacy protection features, such as emphasizing incognito browsing mode, which can ensure that your browsing history is not recorded; with ad blocking function, which can effectively block ads that may contain tracking codes; and anti-tracking features, which can identify and block various tracking behaviors.
For example, the Firefox browser has an excellent performance in privacy protection. Its private browsing mode can prevent websites from tracking your activities, and it blocks third-party cookie tracking by default.
Secondly, it is also wise to use browser extensions to strengthen the defense line. Efficient privacy protection plug-ins such as PrivacyBadger and uMatrix can identify and block potential tracking behaviors, including identification based on hardware resources. These plug-ins can monitor website requests and block those that attempt to obtain your hardware information.
In addition, it is important to keep the browser and operating system updated regularly. Software developers will continue to discover and fix possible security vulnerabilities and privacy risks. Through regular updates, you can get the latest security patches and privacy enhancements in a timely manner, thereby effectively resisting new privacy threats.
In addition, for some advanced users who have higher requirements for privacy protection, deploying hardware-level protection measures is a good choice. For example, using a hardware firewall or setting privacy protection options at the router level can prevent external networks from snooping on your local hardware information at the physical level.
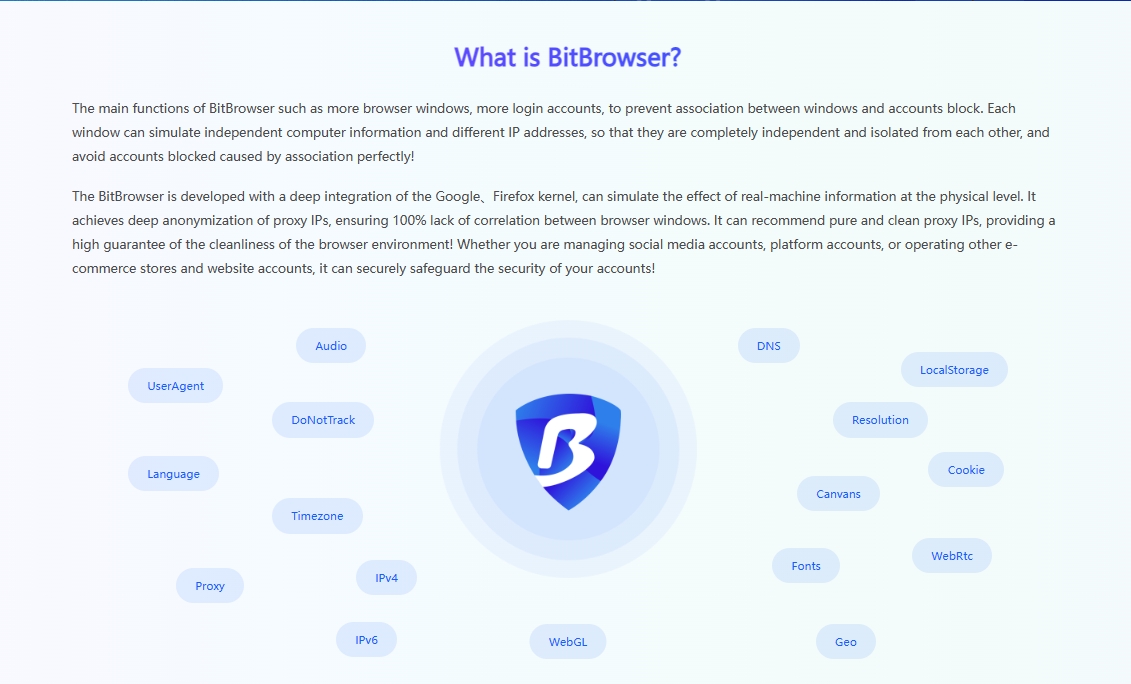
How to use BitBrowser to prevent risks caused by hardware concurrent fingerprints?
BitBrowser is a powerful multi-account management tool. It can generate a unique browser fingerprint for each account, including but not limited to user agent (User-Agent), screen resolution, fonts, plug-ins, hardware concurrency and other information. In this way, BitBrowser can simulate a seemingly independent browsing environment for each window, thereby reducing the risk of abnormal logins caused by hardware concurrent fingerprints detected by the platform.
In addition, BitBrowser also has the following features and functions:
Account information sharing: Team members can share account information without disclosing login credentials, which is conducive to collaboration and can ensure the security of accounts.
Window group control
Batch operation: Users can perform the same operations in multiple browser windows, such as searching, browsing, interacting, downloading, etc. These operations will be synchronized to all open windows, greatly saving time.
For example, if you need to search for the same keywords in multiple windows at the same time, this function allows you to complete it with one click.
User operation simulation: This function performs tasks by simulating the behavior patterns of real users, reducing the risk of being detected as non-human behavior by the platform.
RPA automation
Automated tasks: It can automatically perform tasks with high repetitiveness, such as creating accounts and publishing content. Users can set tasks and let BitBrowser complete them automatically, thereby improving efficiency.
If you need to create multiple new accounts every day, you can set BitBrowser to automatically complete this tedious task.
Enhanced social interaction: RPA automation can also be used to enhance user participation, such as automatically inviting users to like or join a group.
Team collaboration
Permission management: Administrators can set different access rights to ensure that team members can only access the accounts they are responsible for, and strengthen internal security management.
Encryption and security: All sensitive data is stored and transmitted in an encrypted manner, which effectively guarantees data security.
Two-factor authentication: An additional security verification step is added to ensure that only authorized users can access account information.
For example, in addition to regular passwords, user identities need to be further confirmed through mobile phone verification codes and other methods.
Summary:
By deeply understanding new privacy threats such as hardware resource concurrency identification and taking effective protective measures, we can not only defend our privacy rights and interests, but also contribute to building a more secure and trustworthy Internet environment.
Please remember that privacy protection is an endless and protracted battle. When protecting our own privacy, using BitBrowser is undoubtedly a good choice. Download BitBrowser now and get 10 permanent free windows immediately.