
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
How does browser automation leak fingerprint information? A deep analysis of unique characteristics and how to deal with them
Time: 2024-05-31 10:09 Click:
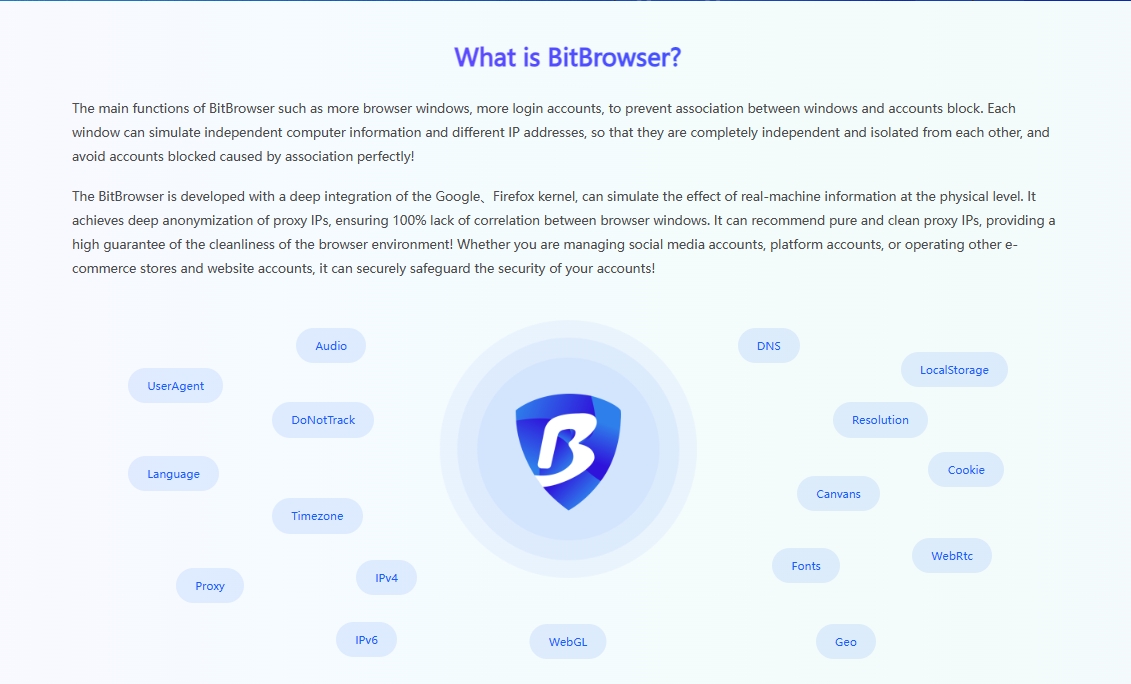
In today's digital world, the analysis of browser's unique characteristics is a sophisticated and ingenious art. It is not just a simple collection of common browser and device information (such as user agent, screen pixel distribution and font list). Instead, it is necessary to deeply explore these characteristics, together with more complex interactive behaviors, to create a "digital identity" that is difficult for others to imitate and unique. The power of this technology lies in that it can not only distinguish different users, but also distinguish whether the user's operation is from real human hands or controlled by some automated process.

On the current Internet stage, automation tools such as Selenium and Puppeteer have shined in many task areas, such as web page detection and data acquisition. And these tools will leave their own unique traces in the browser world during operation. For example, Selenium will leave marks on certain specific properties of browser objects, while Puppeteer will tamper with specific JavaScript object properties, such as modifying window.navigator.webdriver. These traces become the key clues for websites to determine whether users are using automated processes.
In addition to these obvious signs, the behavior patterns of automated processes are also the key to their identification. Compared with real users, automated processes usually show faster operation speeds and more regular interactive behaviors. For example, when filling out a form, real users often have short pauses and mistakes, while automated processes may complete the entire process in one go at lightning speed and amazing accuracy.
Discussion on the website's strategy to deal with automated processes
With the increasing number of automated processes, websites have resorted to various advanced unique feature analysis technologies to deal with them. Once these technologies detect that users may be using automated processes, the website may use a series of tricks, including but not limited to restricting users' operating permissions, banning accounts, and even blocking IP addresses.
The impact of automated tools on the unique characteristics of browsers

Automated tools such as Selenium and Puppeteer have undoubtedly brought significant impacts on the unique characteristics of browsers while improving work efficiency.
User agent personalization: Although these tools allow users to set the user agent string on their own, if the setting is not appropriate, it can easily alert the website.
Changes in the JavaScript environment: As mentioned earlier, these tools will tamper with the browser's JavaScript environment when running, such as setting the window.navigator.webdriver property. These changes are like the user's true intentions being exposed to websites with corresponding detection capabilities.
Residual signatures: When using tools such as Selenium, specific signatures or marks may be left in page elements, network requests, etc. These signatures are like fingerprints for websites, and can easily identify the user's true identity.
So, when using automated tools, users must be extra careful to avoid exposing their true identities due to improper operations. At the same time, websites also need to continuously improve their unique signature analysis technology to cope with the increasingly complex challenges of automated attacks.
How to prevent it?
1. Use local API of BitBrowser
You can directly open the web page through the local API of BitBrowser, bypass the detection of selenium driver by Cloudflare service provider, and then enter the web page for Selenium automation operation.
2. Use RPA robot
Opening the web page through the RPA robot function of BitBrowser can directly bypass the detection of Cloudflare service provider. RPA provides powerful automation capabilities for non-technical users. Even technical novices can achieve professional automation processes through simple steps!
3. Reset SeleniumDriver
You can bypass CloudFlare detection by resetting SeleniumDriver. After using Selenium to open the page detected by CloudFlare, you need to reset SeleniumDriver to bypass the detection.
4. Use Puppteer automation
Puppteer directly calls the browser's DevTool protocol to avoid CloudFlare detection. By using Puppteer automation to open the page, you can also achieve the same function as Selenium, but it is more troublesome to write NodeJS.
Summary:
Analysis of browser unique features is an in-depth means of user identification and tracking. It not only includes conventional information collection, but also involves the exploration of complex interactive behaviors to shape a unique "digital imprint" that can identify users and operation sources. By using BitBrowser's localAPI and RPA robots, it can effectively prevent automation tools such as Selenium and Puppeteer from leaving unique traces and affecting browser features, causing their behavior patterns to be identified. As the most convenient tool to prevent browser unique features, BitBrowser, download now and get 10 permanent free windows immediately.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



