
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
What is a high-anonymity proxy? BitBrowser explained
Time: 2024-07-27 17:19 Click:
In today's digital age, network privacy and security have become important issues that cannot be ignored. With the popularization of the Internet and the rapid development of technology, various proxy services have emerged. Among them, high-anonymity proxies stand out with their excellent concealment capabilities and become the first choice for users who pursue extreme privacy protection. This article aims to deeply analyze the operating mechanism, advantages, application scenarios and how to choose a reliable service provider of high-anonymity proxies, and take you into the mysterious world of this network stealth.

1. High-anonymity proxy: definition and characteristics
High-anonymity proxy, as the name suggests, is an HTTP proxy service that can provide a very high level of anonymity. Compared with ordinary anonymous proxies, high-anonymity proxies are not only more advanced in technology, but also reach new heights in concealing user identities. It not only hides the user's real IP address, but also cleverly disguises itself so that the target server cannot recognize that the request is sent through a proxy.
Specifically, high-anonymity proxies achieve their concealment function by modifying key header information in HTTP requests. These headers include HTTP_VIA, HTTP_X_FORWARDED_FOR, and REMOTE_ADDR. Under the setting of high anonymous proxy, HTTP_VIA and HTTP_X_FORWARDED_FOR will be cleared or set to values that do not expose the proxy identity, while REMOTE_ADDR will be replaced with the IP address of the proxy server. In this way, even the most savvy websites will find it difficult to detect the user's real identity and location information.
2. Working principle of high anonymous proxy
The working principle of high anonymous proxy can be summarized as a combination of "transit station" and "camouflage". When a user initiates a network request, the request will first be sent to the high anonymous proxy server. After receiving the request, the proxy server will perform a series of processing and modifications to eliminate any information that may expose the user's identity. Subsequently, the proxy server sends a request to the target server as its own identity and returns the target server's response to the user. In this process, the user's real IP address is completely hidden and replaced by the IP address of the proxy server.
3. Advantages of high anonymous proxy

Higher anonymity: Compared with anonymous proxy, high anonymous proxy can more effectively hide the user's real identity and location information, reducing the risk of being tracked and identified.
Stronger anti-detection capabilities: Many websites will take measures to detect and block requests sent through proxies. High-anonymity proxies can easily bypass these detection mechanisms with their sophisticated camouflage technology.
Wider application scenarios: Since high-anonymity proxies have stronger concealment capabilities, they can be applied to more scenarios that require high privacy protection, such as web crawlers, data collection, SEO optimization, etc.
Better privacy protection: Using high-anonymity proxies can reduce the risk of user personal information leakage and protect users' network privacy security.
4. Application scenarios of high-anonymity proxies
Web crawlers and data collection: When conducting large-scale web crawlers and data collection, using high-anonymity proxies can effectively avoid the risk of IP being blocked and improve the efficiency and success rate of data collection.
SEO optimization: SEO practitioners can use high-anonymity proxies to simulate users in different regions visiting websites to evaluate the ranking and performance of websites in different regions.
Privacy protection and anonymous browsing: For users who value personal privacy, high-anonymity proxies are an indispensable tool when browsing the Internet. It can help users hide their real identity and location information to prevent tracking and monitoring.
Access to restricted content: In some regions or network environments, some websites or content may be restricted. Using a high-anonymity proxy can bypass these restrictions and allow users to freely access the information they need.
5. How to choose a reliable high-anonymity proxy service provider
When choosing a high-anonymity proxy service provider, users need to pay attention to the following aspects:
Service quality: including proxy speed, stability, availability and other aspects. Users can understand the service quality of the service provider by trying it out or viewing user reviews.
Price protection: Ensure that the service provider has strict privacy protection policies and measures to protect the user's personal information and privacy security.
Technical support: Providing timely and professional technical support services is one of the important indicators to measure the quality of the service provider. Users should be able to get timely help and solutions when they encounter problems during use.
Price and cost-effectiveness: Choose a suitable proxy package and service provider according to your own needs and budget. Pay attention to comparing the prices and service content of different providers and choose a service with a higher cost-effectiveness.
How to choose a high-anonymity proxy service?
BitBrowser provides users with various proxy recommendations. Open BitBrowser to access major IP agents and obtain various types of agents, including ISP agents, residential agents, high-anonymity agents, etc.
Why should we use a high anonymous proxy with BitFingerprint Browser?
The connection between the two is that they can work together to improve the user's network security and privacy protection level. Users can hide their real IP address through the proxy IP first, and then use the fingerprint browser to access the network. In this way, even if the website tries to track the user through the browser fingerprint information, it will be difficult to accurately identify the user's true identity due to the combined effect of the proxy IP and the fingerprint browser. This combination enhances the user's anonymity and makes the user's network activities more difficult to track and monitor.
In some specific scenarios, the cooperation of proxy IP and fingerprint browser can play a greater role. For example, in the field of web crawlers, they can help crawlers simulate the browsing behavior of human users to avoid being identified and blocked by the target website; for users who need to manage multiple accounts at the same time, by configuring different proxy IPs and fingerprint browser environments for each account, isolation and security management between accounts can be achieved.
At the same time, BitBrowser Fingerprint Browser also supports a variety of functions to save time and effort:
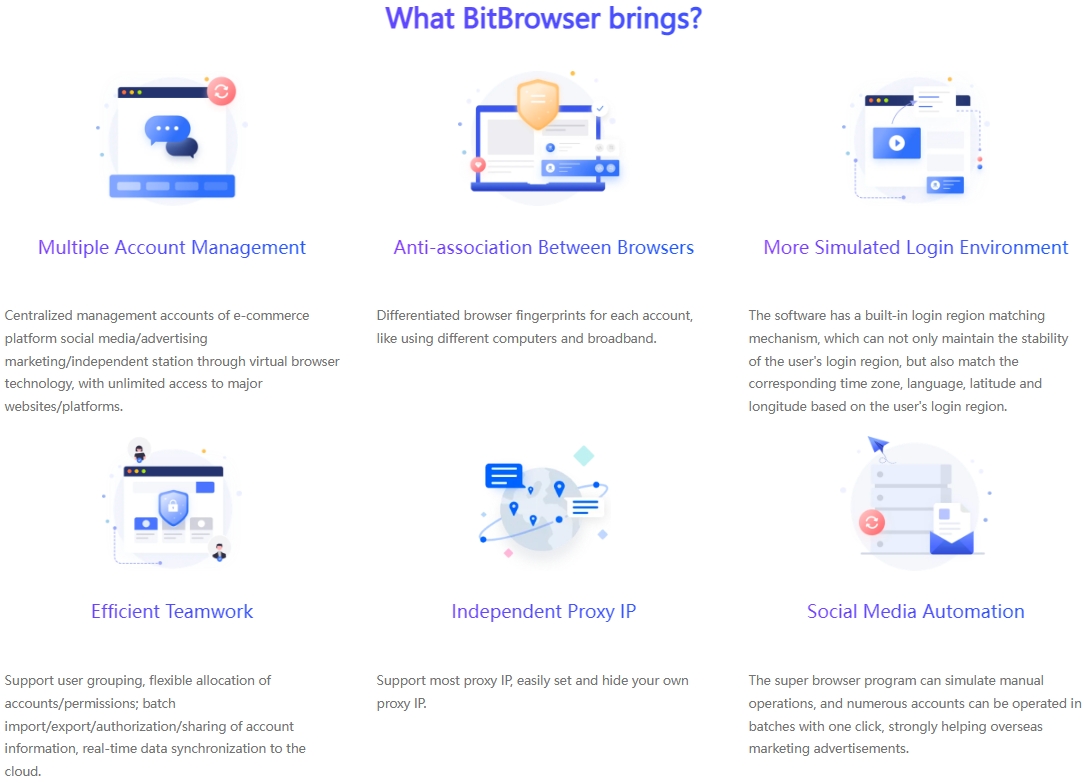
RPA automation function: BitBrowser has RPA (Robotic Process Automation) script support capabilities, and RPA automation process templates are set up internally to assist users in automatically completing a series of automation-related operations. For example, you can set up automatic likes for designated channels, automatic comments, or automatic follow-ups of specific users. Such automated operations can run automatically in the background without manual involvement, thereby saving users a lot of time and improving marketing efficiency.
Window group control: When operating multiple social media accounts for the same promotional activities, the window synchronization function can synchronize operations to all open accounts with one click to ensure uniformity and timeliness, which is very suitable for marketing activities that require the same operations to be performed on multiple accounts.
Summary:
Although you may tend to regard high-anonymity proxies as anonymous proxies, this is not the case. The difference between the two is reflected in the content changes made to HTTP_VIA and HTTP_X_FORWARDED_FOR. Because of such changes, it is difficult for web servers to identify high-anonymity proxies. Therefore, when you need high anonymity, high-anonymity proxies are the best choice. However, it should be noted that such proxies are usually more expensive. In order to achieve better anonymity, high-anonymity proxies are usually used with fingerprint browsers. BitBrowser provides users with a highly anonymous fingerprint anti-association function. Download BitBrowser now and get 10 permanent free windows immediately.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



