
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
How to use IP settings for fingerprint browsers?
Time: 2023-11-22 15:34 Click:
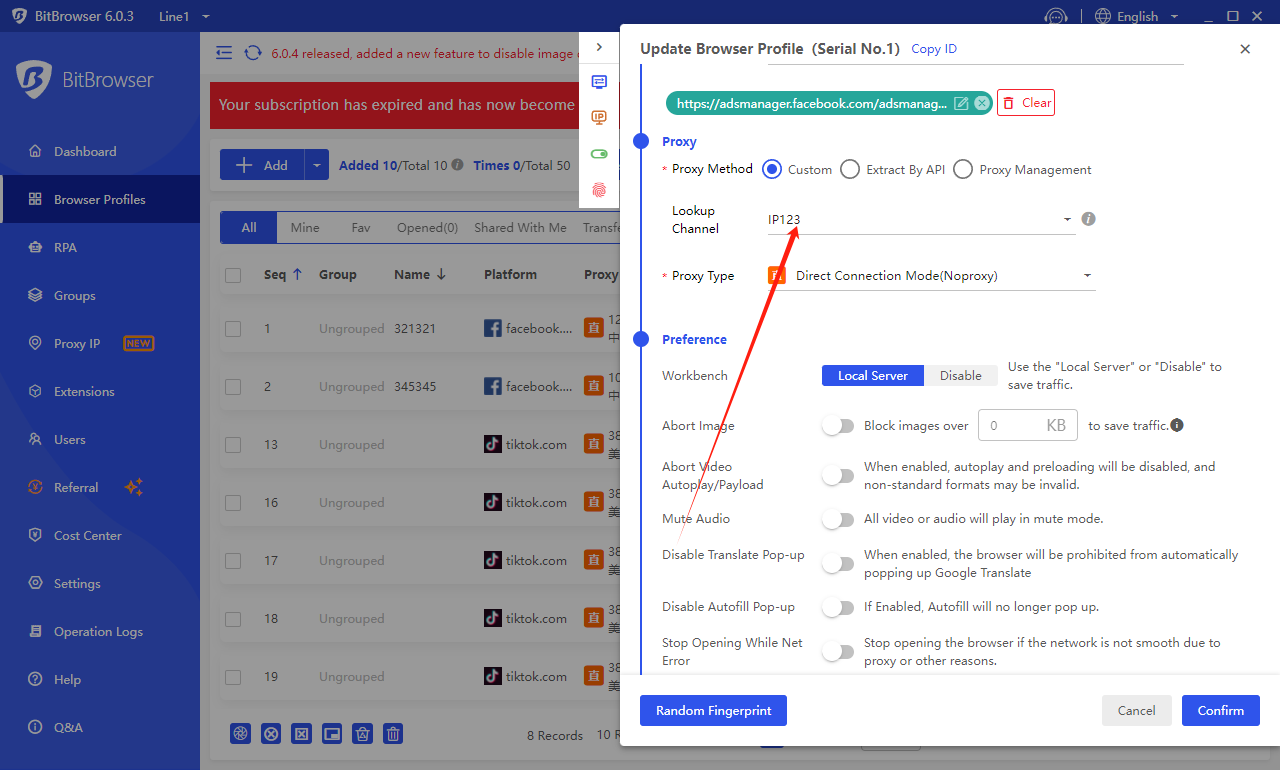
Fingerprint browser is a network browser that can provide anonymous and privacy protection. By using different IP addresses, users can access different websites or services anonymous on the Internet. The following is the steps of how to set the IP address of the bi -fingerprint browser:
Download and install Bitbrowser.
Open the fingerprint browser and select an IP address that suits your needs. You can choose the local IP address, or you can choose a public IP address.
Set the proxy server in the browser. The proxy server can help you hide the real IP address to protect your privacy.
Enter the selected IP address and port number in the proxy server.
Save the settings and close the proxy server.
Set the IP address with fingerprint browsers can bring many benefits. First of all, it can protect your privacy and avoid your real IP address by the website or service. Secondly, using different IP addresses can make your network behavior more anonymous and avoid being tracked or monitored.
In addition, using Bitbrowser's fingerprint browser can allow you to easily switch different IP addresses to better protect your account security. Avoid multi -account login to bring about related troubles at the same time.
When selecting an IP address, you need to pay attention to the following points. First, choose a reliable proxy server to ensure the stability and availability of the IP address. Secondly, pay attention to the location and speed of the proxy server. Choose a proxy server suitable for your geographical location and network speed to improve the experience. Finally, pay attention to the security of the proxy server to avoid using an unsafe proxy server and cause personal information leakage or account.
In short, the use of fingerprint browsers to set the IP address is a very practical technology that can protect personal privacy and account security. By choosing a reliable proxy server and attention related matters, you can better use this technology to protect your network behavior and information security.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



