
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
What is an anti -detect browser and how to choose an anti -detect browser?
Time: 2024-02-22 16:28 Click:
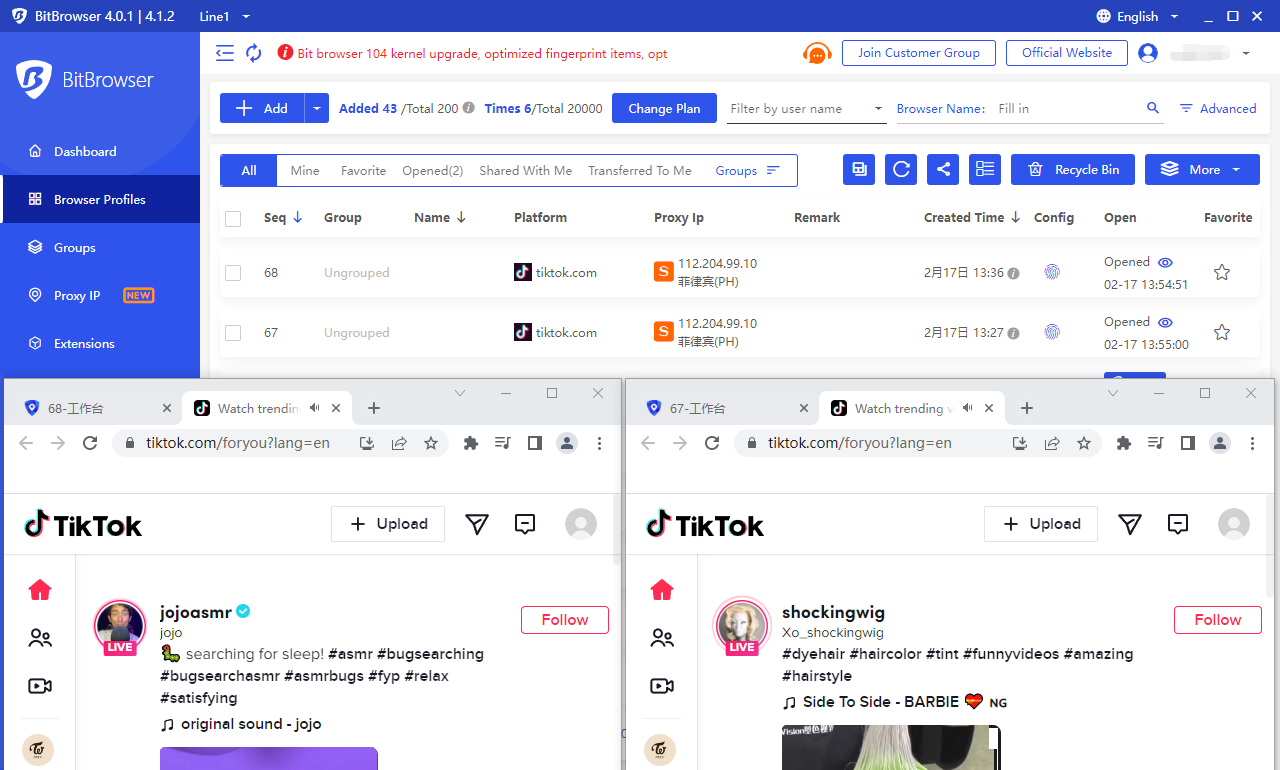
Anti-detect browsers (such as Bit browser) are technical tools used to simulate and manage browser fingerprints at the browser level. These fingerprints are the only identifier generated by the browser, which can be used to identify devices and users. Its main purpose is to simulate and maintain multiple browser fingerprints, allowing users to maintain anonymity on the Internet and prevent tracking and recognition.
In the global network environment, Anti-detect browsers can simulate the fingerprints of different browsers, covering the characteristics of different operating systems, browser types, languages, time zones, resolution and other characteristics, which will help support users' online privacy and reduce advertisers. And the tracking of data collectors.
In addition, the Anti-detect browser also has the ability to automatically manage the browser fingerprint. Through various simulation and management, it reduces the risk of detection and improves the security of user privacy. This technology is widely used in application scenarios that emphasize privacy protection and anti -associations.
What are the advantages of Anti-detect browsers?
1. Privacy protection: Anti-detect browsers can simulate and manage multiple browser fingerprints to keep users anonymous on the Internet. This can prevent your online activities from being tracked and monitored and enhanced personal privacy protection.
2. Tracking prevention: Anti-detect browsers can prevent advertisers, data analysts, and other followers by simulating multiple browser fingerprints, reducing the possibility of being tracked and positioning by users, thereby reducing unnecessary advertising for user exposure And data collection.
3. Prevent recognition: Browser fingerprint is the unique identifier that can be used to identify devices and users. The diversity of Anti-detect browsers allows users to easily switch between different fingerprints to prevent them from being recognized and associated on the Internet.
4. Improve security: Anti-detect browsers can automatically manage the browser fingerprints and reduce the risks detected by the continuous change of fingerprints. This improves the security of user privacy and prevent malicious behavior and attack.
5. Flexibility: Anti-detect browser can simulate different browser fingerprint features, including operating systems, browser types, language, time zone, resolution, etc., allowing users to flexibly switch and manage these characteristics as needed to obtain more individuality Touring experience.
6. Wide application: Anti-detect browsers are widely used in cross -border e -commerce, online advertising protection, and network privacy protection, providing users with a safer and more private network environment.
3. How to choose a Anti-detect browser?
1. Network security and personal privacy: When choosing the right browser, the first thing to consider is whether it protects network security and personal privacy. The browser should have a reliable protective mechanism to ensure that your different account information will not be associated with the platform.
2. Easy to manage multiple accounts: Considering that multiple accounts on different platforms need to be managed at the same time, choosing a browser that can easily manage multiple accounts will effectively improve your work efficiency.
3. Stability and speed: Stable browsers can reduce time wasting due to collapse and freezing pages, and web pages loading faster, thereby improving your work efficiency.
4. Perfect after -sales support: Choose a browser that provides high -quality after -sales support. When any problems, you can provide help and solutions in time.
Bit browser is a browser developed with Google's kernel, which is free and free, supports 10 windows. It can simulate the real machine information, use the proxy IP for in -depth anonymity, and ensure that there is no correlation between all windows. The browser also comes with API interface, RPA automation process design and group control synchronization system. It can perform a multi -window mouse keyboard synchronization operation, window arrangement operation, synchronization operation of the tab, synchronous input of the same text and different text, one -click identification of one -click identification Enter the verification code and other functions.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



