Popular Use Cases Release Notes Resources
How can the Daden account browser prevent the account of the account caused by the IP address?
Time: 2024-05-28 19:21 Click:
Under the sweeping wave of digitalization, the Internet has undoubtedly become the core link of our work and life. However, with the rapid development of the Internet, the defense of network security and privacy is becoming more intense. In order to defend their own network space, many people chose VPN or proxy servers to hide their IP addresses. However, it is worth noting that in certain specific scenarios, such as advertising orientation, network crawlers, social marketing, e -commerce operations and traffic realization, it is not enough to hide the IP address.
What is an IP address?
IP address, synonymous as an Internet protocol address, is like an ID card in the online world. It is a series of binary codes with 32 -bit or 128 -bit, which is used to identify each network of equipment in the boundless network sea. Under the guidance of the TCP/IP protocol, IP address is an essential element of communication. Because of its uniqueness, IP addresses are often used to track users' geographical location, behavior trajectory and even hobbies. Therefore, hidden IP addresses have become an important means for many people to protect privacy.
So, how to simulate multiple IP addresses on your computer?
Some people may choose the road, virtual machines, and as the name suggests, that is, to build multiple virtual operating system environments on physical machines. Each environment has independent hardware resources, including CPUs, memory, hard disks, and network cards. In this way, each operating system can have an independent IP address, thereby realizing the IP address simulation. However, this method also has its limitations, such as large resource consumption, high cost, and permits and maintenance costs of each operating system are a lot of expenses.
Another common method is to use the proxy server.

As a bridge between users and target websites, the proxy server can provide users with multiple proxy IP addresses, thereby achieving the effect of simulating multiple IP addresses on the computer. Users only need to buy some proxy IP addresses and configure them to the proxy server software to easily implement it. However, there are certain risks in this way, such as data leakage, identification of target websites and banning security hazards.
So, is there a method that can simulate both multiple IP addresses and can reach a balance between resource consumption, cost, security, and stability? The answer is yes, that is, the Big Fingerprint browser.
How to simulate a variety of IP address data of Bitbrowser
Bitbrowser is not just a multi -opening account browser. It is also a tailor -made assistant for multi -account operations. While strictly abide by the social media platform login agreement, the Bitbrowser also has a powerful anti -detection function. It gives social media marketing full control of browser fingerprints, enabling sellers to easily access various platforms. The core advantage of the Bitbrowser is its browser fingerprint isolation technology.
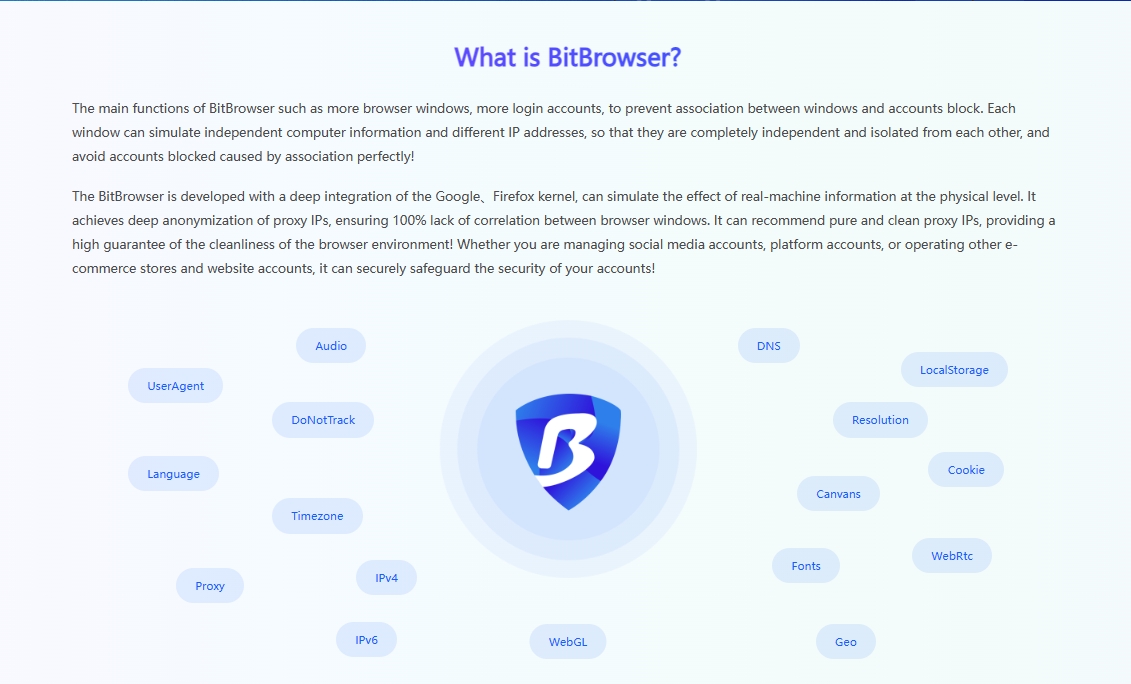
Bitbrowsers are not directly simulated IP addresses, but to simulate browser fingerprints to achieve multi -account login, multi -website launch, multi -channel promotion and other functions. Browser fingerprints, in short, are a series of information logos carried by the browser when visiting the website, such as user agents, operating systems, browser versions, etc. Because each user's browser configuration and usage habits are different, each user's browser fingerprint is also unique. Bitbrowser uses this feature to create an independent virtual browser environment for each account or website, and allocate unique browser fingerprints for each environment. In this way, even if the same browser is used on the same computer, the goals of multi -account login and multiple websites can be achieved through the fingerprint isolation technology of Bitbrowser.
Summarize:
For those who need to simulate multiple IP addresses on the computer, the Bit fingerprint browser is undoubtedly a choice worth trying. It not only has an advantage in resource consumption and cost, but also excellent performance in safety and stability. Through the help of Bitbrowser, users can easily control the network space of the digital era more easily.