Popular Use Cases Release Notes Resources
Are Virtual Private Networks (VPNs) Safe? Should I Choose a Fingerprint Browser or a Virtual Private Network (VPN)?
Time: 2024-07-27 17:13 Click:
In today's era of high Internet penetration, network security and data privacy have become core issues of close concern to the public. Virtual Private Network (VPN), or virtual private network, is a common means of network protection and anonymization, and is regarded by many users as an important tool for protecting online privacy and data security. However, it should be clear that the security of virtual private network (VPN) is not indestructible, but is affected by many factors. This article will deeply analyze the security challenges faced by virtual private network (VPN) to help users more thoroughly understand its working principle, original intention, advantages and disadvantages, and potential risks.
1. Working principle of virtual private network (VPN)

Virtual private network (VPN) mainly builds an encrypted channel to transmit the user's network traffic to a remote server (i.e., virtual private network (VPN) server), and then the server forwards the traffic to the target website or service. Although this encryption method can prevent the user's network traffic from being attacked and stolen by middlemen to a certain extent, it must be recognized that the encryption technology of virtual private network (VPN) is not flawless, and the possibility of being cracked always exists. In addition, the quality and performance of VPN services will also fluctuate due to many factors such as the location of the server, the bandwidth of the network, and the load.
2. Reasons why users use VPNs
The reasons why users decide to use VPN services are rich and varied, mainly covering the following aspects:
Breaking geographical restrictions: A large amount of online content and services are restricted by geographical regions, and VPNs can help users break through such restrictions and successfully access blocked websites and streaming platforms.
Strengthening privacy and data security: In an insecure network environment such as public Wi-Fi, VPNs can mask the user's real IP address, effectively avoiding being tracked by hackers and intelligence agencies and data theft.
Meeting corporate network access needs: Many organizations use VPNs to ensure that remote employees can securely access internal resources and ensure the confidentiality and integrity of data transmission.
3. Analysis of the pros and cons of virtual private networks (VPNs)
Using virtual private networks (VPNs) has both significant advantages and potential disadvantages:
Advantages:
Data encryption protection: VPNs use encryption technology to protect users' network traffic and ensure the security of data during transmission.
IP address hiding: It can hide the user's real IP address to prevent tracking and positioning by third parties.
Secure network transmission: The encrypted channel provided can effectively resist man-in-the-middle attacks and prevent user data from being stolen.
Disadvantages:
Slowed network speed: The encryption and routing process of VPNs may cause network speed to decline, which will have a negative impact on the user's experience.
Higher costs: Some high-quality VPN services may require users to pay a certain fee.
Legal compliance risks: In some countries and regions, the use of VPNs may violate local laws and regulations, and users need to understand and strictly abide by relevant regulations.
4. Security Challenges Faced by Virtual Private Networks (VPNs)

Even though VPNs have many security features, they still have to deal with a series of security challenges:
Security issues of VPN services themselves: Some VPN service providers may have security vulnerabilities, such as weak password policies, insecure server configurations, or failure to perform security updates in a timely manner. These risks may cause users' network traffic to be leaked or attacked.
Limitations of encryption technology: Although VPNs use encryption technology to protect data transmission, these technologies are not absolutely reliable. With the continuous development of technology, hackers and intelligence agencies may develop more advanced cracking methods to attack the encrypted channels of VPNs.
Risk of DNS leakage: In certain circumstances, VPN connections may experience DNS leakage. When the user's device first performs DNS queries before connecting to the VPN server, these queries may be intercepted by a third party and used to track the user's online activities.
Legal and regulatory risks: In some countries and regions, the use of VPNs may violate local laws and regulations. Users need to be familiar with and follow local laws and regulations to avoid legal risks and penalties.
5. Comparison between Virtual Private Network (VPN) and BitFingerprint Browser
For those users who strive for high anonymity, BitFingerprint Browser may be a better choice. BitFingerprint Browser prevents websites and advertisers from tracking by modifying browser fingerprints and hiding users' online activities. Compared with Virtual Private Network (VPN), BitFingerprint Browser is more direct and efficient in protecting user privacy. Imagine having to run multiple accounts with regular browsers and VPNs, but pay attention to privacy. It's like completing a "Mission Impossible" stunt.
Using a fingerprint browser like BitBrowser, you can operate multiple accounts from the same browser interface using separate browser fingerprints. These unique fingerprints can be activated in a few minutes, and when you switch between profiles, such as using tabs in the browser, it is more convenient to operate multiple browser windows.
How to choose a fingerprint browser?
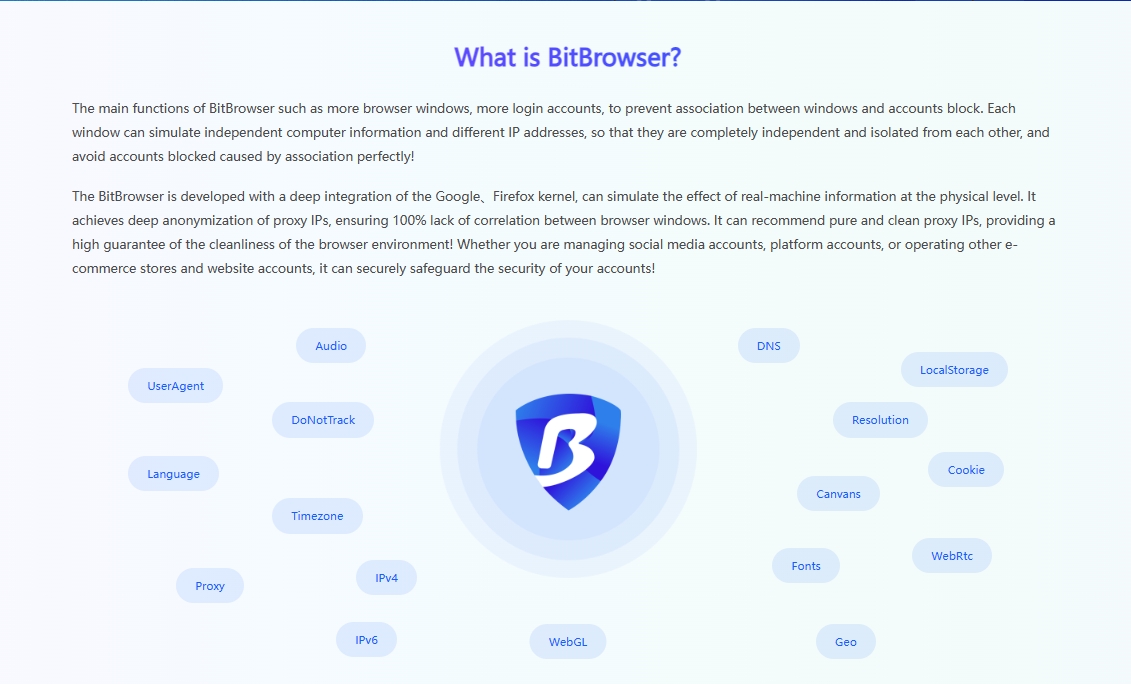
In the process of managing multiple accounts, it is also a common problem that the account is blocked due to the environment in which the account is located or the IP is associated. Therefore, using fingerprint browser to manage multiple accounts will be more efficient and secure:
Multi-account management:
Fingerprint browser allows users to create a separate browser environment for each account. One of its key functions is to customize and manage the "fingerprint" of each browser environment. The fingerprint mentioned here covers user agent, screen resolution, font, operating system version, etc. By customizing these fingerprints, the probability of being tracked and identified by the website can be reduced, thereby adding an additional protection barrier to your account.
IP address and location management:
With the help of fingerprint browser, you can configure a proxy server for each account, which helps to avoid the account being marked or locked by Facebook due to abnormal IP address.
Cookie and cache isolation:
Each fingerprint browser environment can independently store the account's cookies and cache data, and the information between different Facebook accounts will not interfere with each other. This is very helpful for preventing potential data leakage between accounts.
Summary:
The security issues of virtual private networks (VPNs) are complex and diverse. Although virtual private networks (VPNs) provide security guarantees such as data encryption and IP address anonymity, they also face risks such as limitations of encryption technology, service security, and legal supervision. Using a fingerprint browser such as BitBrowser is undoubtedly a more convenient multi-account solution, protecting your multiple accounts at the same time. BitBrowser's anti-detection fingerprint system combined with an independent IP can better protect the security of your account. Download BitBrowser now and get 10 permanent free windows on a first-come, first-served basis.