
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
Click to learn about the six parameters that cannot be ignored in fingerprint browsers
Time: 2024-07-27 17:26 Click:
During the anti-tracking operation, the key to success is not just relying on the quality of the agent. With the continuous innovation of network tracking technology, the current anti-tracking strategy must implement multi-dimensional and precise protection measures. In particular, in the implementation of high-quality multi-account operation processes, browsers must be able to imitate and blur a large number of device feature identification parameters, covering those subtle details that are rarely valued in traditional identification.

The following are some key device feature identification simulation and blurring technologies, which together form the key support for contemporary anti-tracking work:
Dynamic graphic identification construction: The browser can imitate the rendering process of the Canvas element in HTML5 to create graphic outputs similar to real devices. Different from conventional Canvas fingerprints, dynamic graphic identification construction will dynamically draw graphics based on page loading status or user interaction behavior, making each generated fingerprint unique, greatly increasing the complexity of anti-tracking.
WebGL interface full-scale emulation: WebGL is not only an interface for drawing three-dimensional graphics, it also includes a lot of information about device performance and characteristics. High-performance anti-tracking browsers will deeply emulate the call operations of the WebGL interface to generate graphics output and performance data similar to real devices. This emulation is not limited to graphics drawing, but also covers the simulation of complex rendering effects such as texture, lighting, and shadows.

Emulation of audio environment characteristics: AudioContext fingerprints are generated based on the characteristics of device audio hardware. In order to blur this fingerprint, the browser can emulate the audio hardware characteristics of different devices to create a unique AudioContext fingerprint. Given the huge differences in the characteristics of audio hardware, this emulation can effectively increase the recognition difficulty of the tracking system.
WebRTC network address hiding: WebRTC technology allows browsers to communicate with each other through video and audio, but at the same time it will expose the user's real network address. In order to prevent the tracking system from obtaining the user's real network address, the browser can use a network address hiding strategy. This strategy can use relay servers or other technologies to forward communication data, so that the tracking system cannot directly obtain the user's real network address.

ClientRects layout interference: ClientRects is a JavaScript function used to obtain the position and size of page elements in the window. By imitating or interfering with the layout or position of elements, the browser can generate a unique ClientRects fingerprint. Since the changes in page layout and element position are dynamic, this interference strategy can effectively increase the identification difficulty of the tracking system.
TLS handshake information fuzzification: TLS fingerprint is generated based on the TLS encryption protocol. It contains the data transmitted by the client during the TLS handshake process. In order to fuzzify the TLS fingerprint, the browser can simulate different TLS client configurations and parameters to generate TLS handshake data similar to the real device. This fuzzy strategy can prevent the tracking system from accurately identifying the user's TLS fingerprint.
Random allocation of font sets: Font sets are font families installed on devices. They are also a commonly used identification factor. In order to blur the fingerprint of font sets, browsers can randomly select or simulate different font sets, so that the tracking system cannot identify the device based on the font set. This random allocation strategy can increase the difficulty of identification of the tracking system and improve the success rate of anti-tracking.
Select BitBrowser Fingerprint Browser for Anti-Detection:
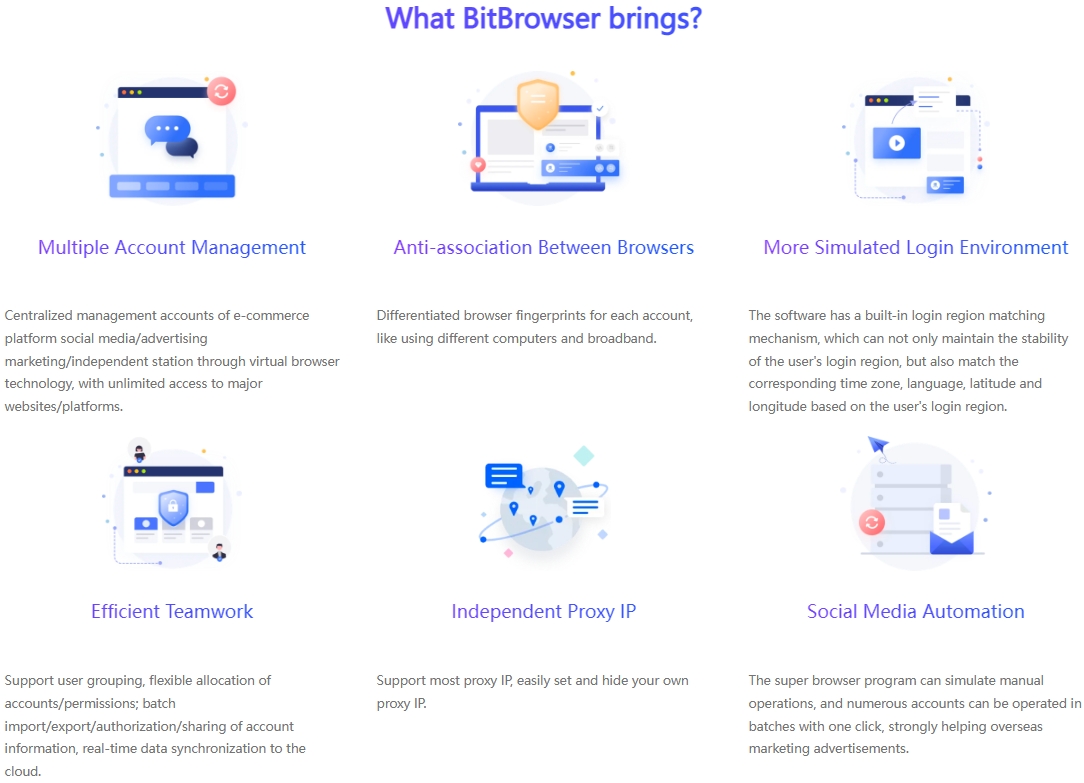
Innovative Breakthrough in Multi-Account Management:
BitBrowser has pioneered the construction of a new multi-account management system, creating an unprecedented operating space for users. At present, users can carefully set exclusive and unique fingerprint information for each account to create a browser environment unique to the account. This move enables each account to have an independent network identity, which effectively protects the privacy and security between accounts. What is particularly noteworthy is that BitBrowser can support users to manage hundreds of social media accounts at the same time, and each account can have its own unique and independent browser environment, which effectively achieves isolation between accounts and efficient management mode.
Flexibility of proxy network configuration:
In order to fully meet the diverse needs of different users, BitBrowser fully supports multiple categories of proxy network configuration methods. Users can customize a dedicated proxy IP for each account according to their actual needs, effectively ensuring that the online behavior of each account does not affect each other, and excellently realizing the independence of account activities. This highly customizable configuration mode gives users more significant flexibility and convenient experience.
Automation transformation of RPA process templates:
In order to further improve user work efficiency, BitBrowser has grandly launched the RPA (Robotic Process Automation) function. These carefully planned automation templates can automatically complete a series of common operations, such as account login, content browsing, post publishing, etc. Users only need to set the process steps in advance to easily achieve the automated execution of batch operations, which greatly saves manpower and time costs and comprehensively improves the overall operational efficiency.
Summary:
When implementing anti-tracking work, users need to implement multi-dimensional and precise protection measures. By simulating and blurring as many device fingerprint parameters as possible, the recognition difficulty of the tracking system can be effectively increased, and the success rate of anti-tracking can be improved. At the same time, choosing a top-level fingerprint browser is also extremely critical. BitBrowser can help users simplify the configuration process and improve the efficiency and quality of anti-tracking. Now you can get 10 permanent free configuration files by downloading BitBrowser. Click to get them.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



