
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
How to detect proxy and use it correctly? A must for multi-account e-commerce sellers
Time: 2024-05-07 14:23 Click:
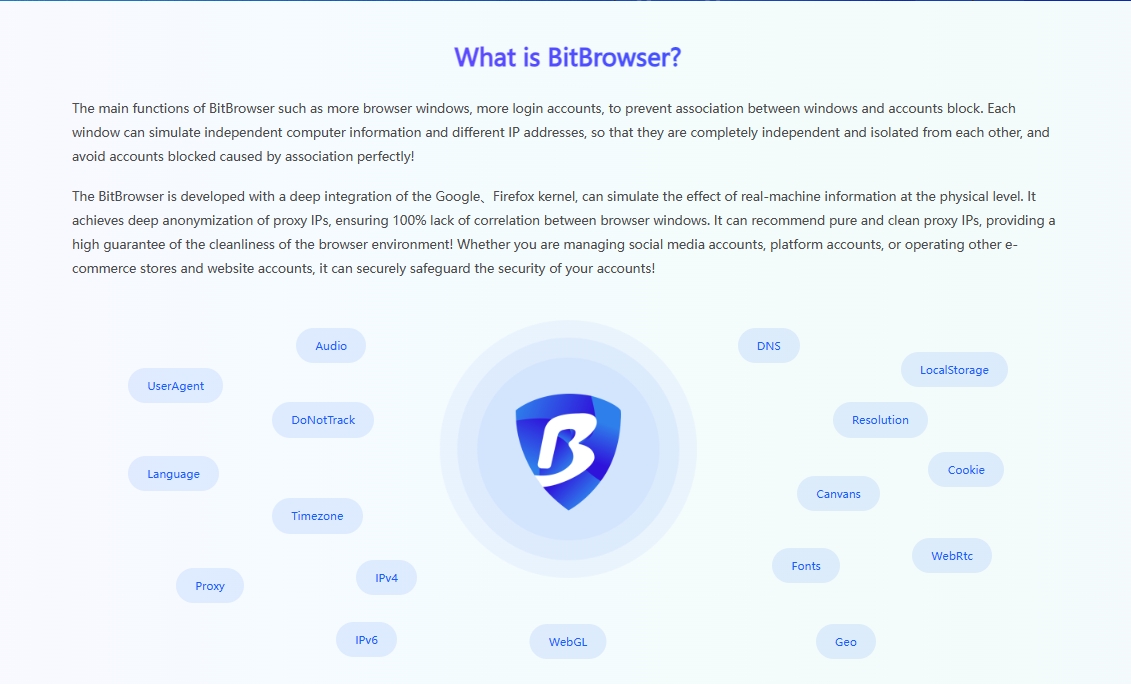
If you want to use multiple accounts on the Internet for e-commerce operations, one of the most important issues is to reasonably avoid multiple account associations. Once associated, it is extremely easy to be banned, which will lead to years of operational failure. In order to use it reasonably and safely Multiple accounts BitBrowser and IP are the most important parts. By matching BitBrowser with IP, you can generate a separate physical environment for each window to achieve absolute isolation and avoid association and ban. In this article you will learn why Proxy IP and fingerprint browser are so important, and what roles they play respectively.
IP proxy function:

In a virtual network, the IP address is like a digital passport, given by the Internet service provider, identifying your online identity information, while the proxy is like an invisibility cloak, allowing you to hide your real IP unknowingly to remain anonymous or disguised Browse the Internet in a comfortable manner.
Proxy IP has many important functions:
1. It can hide the user’s real IP address, protect user privacy and anonymity, and help users bypass geographical restrictions, access restricted content or avoid being tracked; it can also bypass certain websites or services’ access to specific regions or IP addresses. limit.
2. Proxy IP can also provide users with an additional layer of security, filter malicious traffic and attacks, and protect users' devices and data from potential threats.
3. Proxy IP can improve network performance and response time by selecting a proxy server with a similar geographical location, and even provide faster network connections and lower latency.
4. Some proxy servers also have data caching and compression functions, which can reduce the amount of data transmission and improve bandwidth utilization and loading speed.
What types of IP proxies are there?

IP addresses are mainly divided into three categories: data center IP, residential IP and mobile IP. Each of them has unique characteristics and uses, and also affects the risk of account ban. Data center IP is often closely connected to large enterprises or data centers. Residential IP is closer to the daily usage habits of ordinary users. Mobile IP is elusive due to its dynamic nature, adding a higher security factor to online businesses.
Click to read: How should you choose a proxy? About IPV4 and IPV6 / How should you choose a proxy? About SOCKS and HTTPS proxies
1. Residential proxy IP
Residential proxy IP is divided into static and dynamic IP:
Dynamic residential IP refers to the IP address exclusive to real residential users, just like the Wifi IP address of your own home, your next door neighbor's, your friend's home, etc. We call it dynamic housing, and some also call it real-person IP, civilian IP, home IP, private IP, etc. Since we are using the idle resources of real user IPs, that means dynamic residential IPs are switched and changed.
Static residential IP (i.e. fixed residential IP) is a real residential IP purchased directly from an Internet service provider, and its attributes are residential. Static residential IPs are best suited for use cases that require long-term or permanent use, fixed, and no need to switch IPs. That is, you can use a specific IP, and this IP is fixed. This is suitable for long request sessions where you can use the IP continuously.
2. Data center proxy IP
Data center IP (i.e. computer room IP) is a machine-generated IP provided by the data center network. It is usually used for large-scale crawling of non-complex target websites. The computer room IP is generated by the machine and is fixed. Data center networks provide machine-generated IPs, often used to crawl non-complex target websites at scale. Since the computer room IP is generated by the machine and is fixed, the possibility of being detected is relatively high, but the price is cheap.
3. Mobile phone agent IP
Mobile IP refers to real residential IPs connected through cellular (3G/4G networks). Note that these IPs are not connected to the Internet through WIFI or wired connections (in other words, if the user is using WIFI, it will be considered a residential IP ). Mobile IP is typically used primarily to locate highly sophisticated websites and collect mobile-specific network data. For example: used to detect the advertisements you place online to see whether the advertisements are accurately served on mobile devices of different providers.
How does a website detect the disguise of an agent?

Websites rely on browser fingerprinting and other related technical means to identify the existence of agents. They will pay close attention to hosting service providers. Those conspicuous business logos are the "leakers" of data center IP. At the same time, frequent changes in IP addresses will also cause the website to be alert, which is a clear sign of using a proxy or VPN, or the time zone, geographical location and other data of the device information you are using may also risk revealing the real proxy. In addition to IP address, geolocation API, language and WebRTC are also key clues for websites to detect proxies. Geolocation API can reveal your true location, and the language should match the country or region set by the proxy. WebRTC is one of the functions of the browser. , may also become a hidden danger for your identity to be exposed.
How to use agents wisely?
When choosing an agent, be sure to match it with your business needs. During the critical stages of account creation and management, residential proxies are favored because they more closely match real user behavior. When multiple accounts need to be operated at the same time, the sharing feature of mobile agents shows unique advantages. With the help of professional browser fingerprint management tools such as BitBrowser, you can protect your online business more comprehensively. BitBrowser can block or set all key parameters to ensure that you can hide your true identity even under mechanisms such as WebRTC. With the all-round protection of BitBrowser, your online business will be more resilient and will not be afraid of the risk of being banned, allowing you to focus on business development and innovation without any distractions.
Summarize:
Using BitBrowser with IP can better allocate your multiple accounts in independent environments, avoiding the trouble of multiple account associations, and making operation more convenient. If you have not experienced BitBrowser, you may wish to go to BitBrowser Find out at Organ Network, join the ranks of successful companies, and use our technology to ensure the security of your online business and start a smooth and worry-free online business journey.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



