
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
How to check the reliability of fingerprint browser, several common methods
Time: 2024-05-13 18:22 Click:
As online privacy and security become increasingly important, anti-browser detection has moved beyond simple digital fingerprint changes into entirely new territory. Today, we’ll explore the two core missions of anti-detection browsers and provide you with some innovative ways to verify that these browsers are reliable enough at protecting your data.
Mission One: Deep Personalization and Simulation
Anti-detection of browsers no longer involves simply changing a user’s digital fingerprint. They can now simulate a variety of devices, network environments, and user behaviors to provide users with deeper privacy protections. This includes simulating different operating systems, browser versions, hardware parameters, geolocation, network speeds, etc. Through deep personalization and impersonation, anti-detection browsers help users avoid being tracked by websites and advertisers, thereby protecting their online privacy.
Mission 2: Active defense and fraud detection
In addition to masking a user’s true identity, modern anti-detection browsers also feature proactive defense and fraud detection capabilities. They monitor users' online activity in real-time and automatically block potential threats such as malware, phishing sites, and fraud.
In addition, some advanced anti-detection browsers also have intelligent fraud detection functions. They analyze a user's online behavior and compare it with the normal behavior of other users to identify and block any unusual or suspicious activity.
How to verify the reliability of anti-detection browsers?
Verifying the reliability of anti-detection browsers requires a comprehensive approach. Here are some suggested steps:
Independent testing: Use multiple independent online services to check your digital fingerprint and browser configuration. These services should cover a variety of parameters and data volumes to ensure that your anti-detection browser is effectively protected on all fronts.
Simulated attacks: Try to simulate various online attacks and fraud behaviors to test the defense capabilities of anti-detection browsers. This can help you understand whether your browser is able to detect and block potential threats in a timely manner.
Website detection: There are many services on the Internet that can verify your digital fingerprint data. They are sometimes called scanners. With their help, you can:
Understand how and what data various websites and their anti-fraud systems look at.
Find loopholes and make changes to ensure your digital fingerprint matches your needs.
Common testing websites:
1.Whoer.net
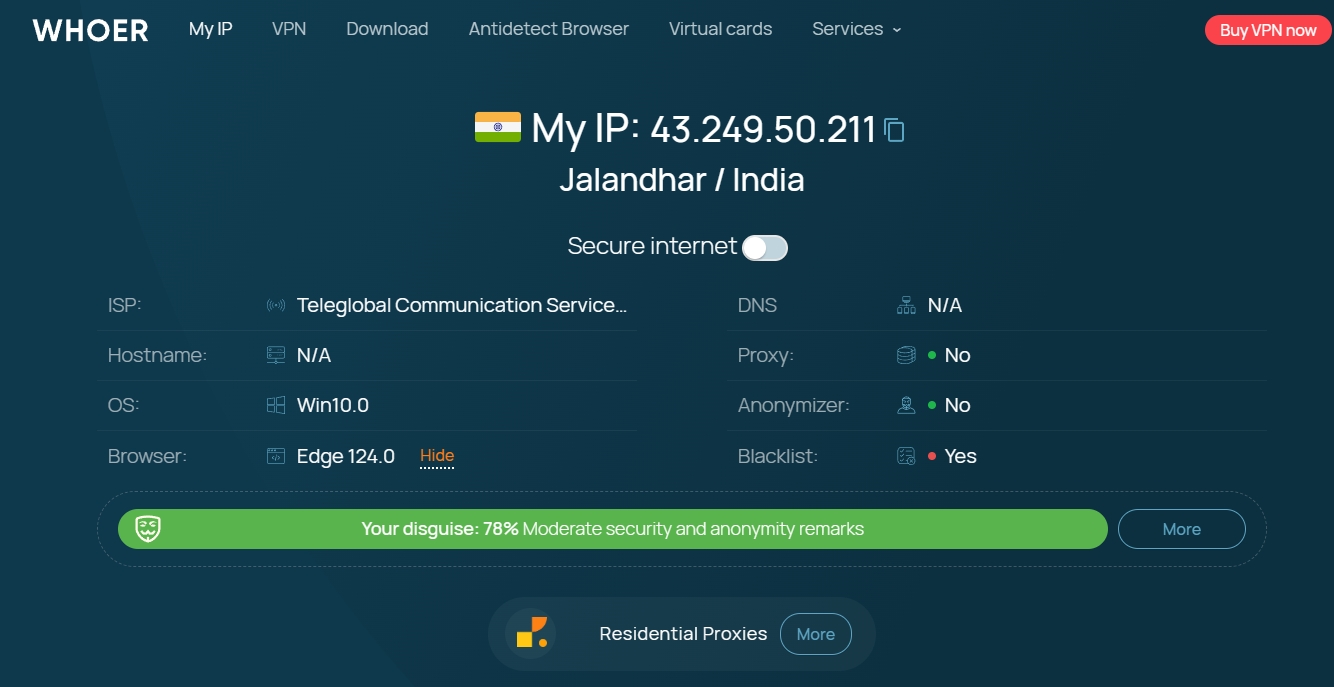
When visiting this website, the service will automatically show you your:
intellectual property
supplier
Host
operating system
browser
DNS domain name
Whether you use a proxy or VPN
2.ipdog.io
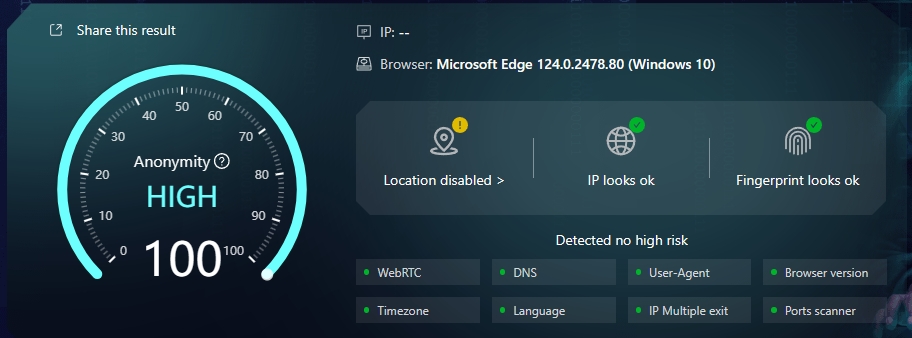
IPdog is a website that focuses on IP detection and browser fingerprinting. It uses DNS leaks, WebRTC leaks, UA detection, time zone detection, geographical location detection, and operating system detection as the core detection items of the website. It is presented intuitively in the form of level warnings, and can also be quickly Perform similarity comparisons on canvas fingerprints, WebGL fingerprints, font fingerprints, and audio fingerprints to clearly understand browser fingerprint details and better protect your personal identity data.
3.browserscan.net
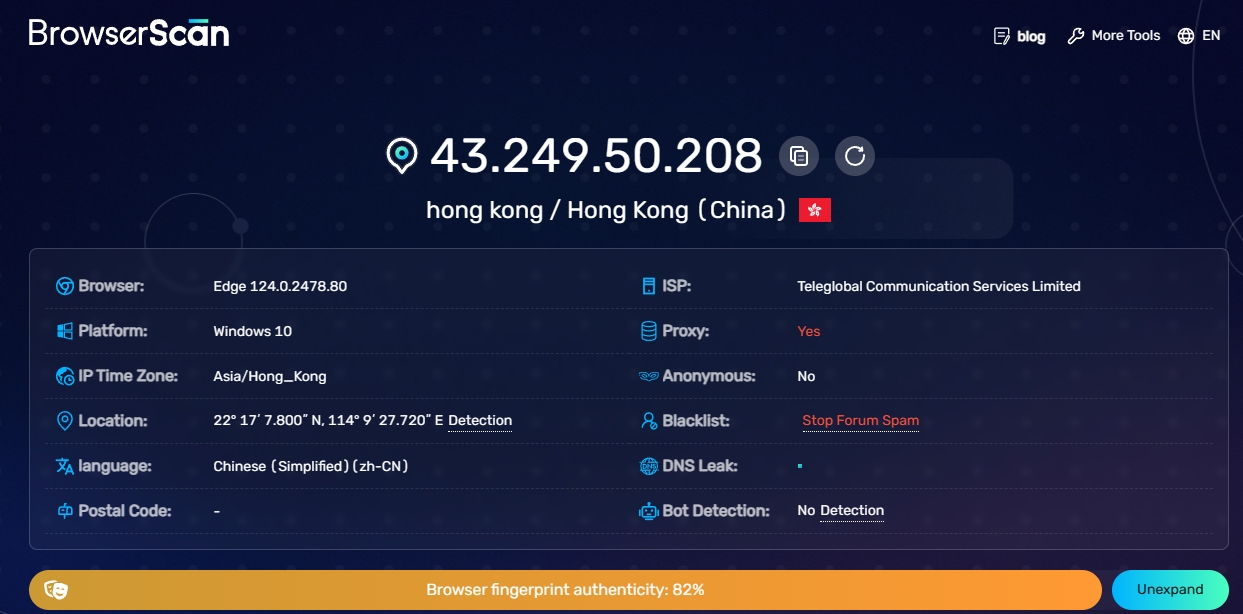
This is a tool to quickly analyze your browser fingerprint. It provides an easy way to quickly check your browser fingerprint, including detecting installed plug-ins, font list, screen resolution, etc. It can also detect whether WebRTC Reveal your real IP address.
Summarize:
In fact, so far, there is no perfect anti-detection browser that can 100% hide the fact that you are changing data. This is mainly because, depending on many parameters, the security system can detect that someone is trying to change his data. For example, this is true in terms of fonts, WebRTC, source browser settings, etc.
To deal with this problem, most of the top anti-detection browsers will automatically pick out fingerprints for you that are adapted to your device. For example, BitBrowser only uses the digital fingerprints of real users and makes all internal parameters compatible with each other. Taking into account the characteristics, this can make the user's data as close as possible to the data of ordinary users.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



