
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
A complete introduction to all proxy IP types. This article is enough to understand proxy IP.
Time: 2024-07-27 16:25 Click:

We all know that to prevent multi-account business from being blocked, an effective way is to match anti-detection browsers such as BitBrowser with reliable proxy solutions. BitBrowser has conducted a detailed analysis on how to choose proxy business. In this article (How to choose a proxy suitable for your business, detailed answer.), but proxies are like guides in a complex maze. They exist in various forms, such as online proxies, HTTP/HTTPS proxies, SOCKS4/5 proxies, dedicated and shared proxies, open and anonymous proxies, and even elite and reverse proxies, which are dazzling. This article will take you through this fog and unveil the mystery of these proxy types one by one.
The essence of proxy: bridge and intermediary
Imagine that the proxy server is like a bridge between you and the Internet. It stands there quietly, receives your requests, and then takes these requests across the ocean of the network to the target web server. After the server has processed it, the results will be returned to you through this bridge. This process is simple and efficient, greatly enriching our network experience.
Proxy Classification: Multi-dimensional Analysis
There are many ways to classify proxies. We can explore them in depth from multiple dimensions such as protocol, anonymity, usage mode, data processing, etc.
Protocol Dimension: The Comparison between HTTP, HTTPS and SOCKS

HTTP Proxy: As the most common proxy type on the Internet, HTTP proxy communicates with the web server through the Hypertext Transfer Protocol (HTTP). It is suitable for most web browsing scenarios, but it should be noted that SSL certificate verification problems may be encountered when dealing with HTTPS encrypted websites. Despite this, HTTP proxy is still widely used in crawlers, data collection and other fields due to its simple and efficient characteristics.
HTTPS/SSL Proxy: In order to solve the shortcomings of HTTP proxy in HTTPS website access, HTTPS/SSL proxy came into being. This type of proxy ensures the security of data transmission by adding SSL layer encryption, protecting the user's privacy information from being leaked. Therefore, when transmitting sensitive information (such as online banking transactions, login password input), HTTPS proxy has become an indispensable choice.
SOCKS proxy: Unlike HTTP and HTTPS proxies, SOCKS proxies work on the lower-level TCP/IP protocol. They can not only transmit HTTP and HTTPS traffic, but also support a variety of other protocols. This versatility gives SOCKS proxies a unique advantage in traversing firewalls and achieving anonymous access. In particular, SOCKS5 proxies have added additional security features to further enhance the security of connections.
BitBrowser has done a more detailed analysis of HTTP, HTTPS and SOCKS proxies. You can learn more about it through this article: (How should you choose a proxy? About SOCKS and HTTPS proxies).
Other dimensions: anonymity, usage patterns and data processing
In addition to the protocol dimension, proxies can also be classified according to anonymity, usage patterns and data processing methods. For example, anonymous proxies and elite proxies perform well in protecting user privacy; dedicated proxies and shared proxies differ in usage patterns; and reverse proxies are more used for server load balancing, security protection and other aspects.
Proxy classification based on anonymity and their respective characteristics
Transparent proxy
Transparent proxy, also known as intercepting proxy, inline proxy or forced proxy, belongs to the category of proxy that does not make any changes to the request and response data. Because of this, they cannot provide any anonymity protection at all, and your real IP address is completely exposed to the target website. This type of proxy often appears in public Wi-Fi hotspots, and its purpose is to limit access rights or cache content to speed up delivery.
Anonymous proxy
Anonymous proxy modifies the information in the HTTP header, replaces your real IP address with the IP of the proxy server, and adds forwarding instructions to hide your identity to a certain extent. Although the website can detect that the connection is completed through the proxy, it cannot track your original IP address. This type of proxy provides you with basic anonymity protection and can support a variety of different protocols.
Elite anonymous proxy (high anonymous proxy)
Elite anonymous proxy or high anonymous proxy has reached a higher level in protecting user privacy. Not only will they replace the IP address, they will also remove all HTTP header information that may leak user information, and will not add any forwarding instructions. In this way, the website cannot distinguish between requests from elite anonymous proxies and requests from ordinary users, providing users with the highest level of anonymity protection. For crawlers or crawling tasks that require high confidentiality, elite anonymous proxies are essential tools.
In this article of BitBrowser, we have detailed what high anonymous proxies are and how to obtain them. Click to visit: (What is a high anonymous proxy? BitBrowser detailed explanation)
Proxy types based on IP sources
Data center proxies
Data center proxies are deployed on specially configured servers with high-bandwidth connections and optimized software configurations to ensure optimal performance. Data center proxies are usually fast, low-latency, and can also provide elite anonymity, which is particularly suitable for most commercial purposes, especially automated scripts and robot operations. However, due to geographical and quantitative limitations, data center proxies may not be as diverse as residential proxies.
Residential proxies
Residential proxies are derived from IP addresses used by real users at home. These proxies realize their value by "renting" them to users in need, such as as part of residential VPN services. The advantage of residential proxies lies in their wide geographical distribution and large number, which makes them less likely to be identified and blocked. Although they may not be as fast as data center proxies, the diversity and authenticity of residential proxies make them ideal for many corporate applications. 922S5 proxy is one of the most reliable residential proxy service providers in the market, with excellent performance in speed, stability and security. As a partner of BitBrowser Finger Browser, 922S5 provides you with the best overseas residential IP service. We have made a detailed introduction in this article. Click to learn more: (Best overseas residential IP provider recommendation | How to use 922S5 proxy in BitBrowser?).
Comprehensive analysis of proxy types based on usage methods
Open proxy (public proxy)
Open proxy, also known as public proxy, is a proxy service that can be freely accessed without any identity verification. Although its free and easy-to-access features have attracted some users, the potential security risks are extremely prominent. Due to the lack of effective protection measures, such proxies can be easily used by hackers to steal user information, and their stability and reliability are difficult to guarantee. For example, when some users use open proxies to access the Internet, they may suddenly encounter disconnection or extremely slow access speeds. Or, users' personal information is obtained by hackers without knowing it, causing serious losses. Therefore, for those application scenarios that have strict requirements on data security and stability, such as network operations and financial transactions involving important business secrets, such proxies must not be used.
Closed Proxy (Private Proxy)
Compared to open proxies, closed proxies are also called private proxies. Such proxies use a strict identity authentication mechanism, and only authorized users can access them, thereby effectively preventing unauthorized use and the risk of data leakage. Based on the difference in usage, closed proxies can be further divided into dedicated proxies and shared proxies.
Dedicated Proxy (Private Proxy): This type of proxy is completely owned by a single user and can provide super high performance and security. Dedicated proxies come in handy when it comes to ticket sales or web crawling, which requires high performance and security. Since there is no sharing of resources with other users, dedicated proxies ensure that users have stable bandwidth and independent IP addresses, greatly reducing the possibility of being blocked. For example, when buying tickets for a popular concert, if you use a dedicated proxy, you can successfully buy tickets first with a stable network connection and an independent IP address.
Shared proxies: Unlike dedicated proxies, shared proxies allow a certain number of users to access the same IP address at the same time. Although this can reduce the cost of use for a single user, the bandwidth speed and stability may be greatly reduced because resources are shared. For example, if multiple users are using a shared proxy to download a large amount of data at the same time, the download speed of each user will be affected. Moreover, if one of the users does not behave in a standardized manner, such as frequently sending spam or conducting malicious attacks, it may also cause the entire proxy IP to be blocked, affecting all users using the IP.
Private rotating proxy: As an advanced form of closed proxy, private rotating proxy uses a scientific and reasonable allocation mechanism to allocate IP addresses in the proxy network to a small number of users in turn. This method not only ensures that users can obtain stable bandwidth and independent IP addresses, but also effectively avoids the risk of being blocked due to long-term use of the same IP. Some providers have also launched exclusive rotating proxy services, that is, only one user uses a specific proxy at a time, which further enhances security and stability. For example, when conducting large-scale network data collection, using private rotating proxies can effectively avoid being identified and blocked by the target website.
Web proxy server and CGIWeb proxy
In addition to the above-mentioned proxy types based on authentication methods, there is also a special form of proxy - Web proxy server. This type of proxy executes the steps of proxy service on the website, allowing users to use the proxy function without tedious configuration on local applications (such as browsers or crawler software). Among Web proxy servers, CGIWeb proxies are particularly special. They receive URLs entered by users through the Web interface (Common Gateway Interface CGI) and access the target page on behalf of users. However, since all data needs to be processed by the host website, CGIWeb proxy has the risk of data leakage and is therefore not suitable for transmitting sensitive information. Moreover, since it cannot be directly integrated into the software for configuration, CGIWeb proxy has significant limitations in business applications. For example, if an enterprise needs to collect and process large-scale data, it is difficult to meet the needs using CGIWeb proxy because it cannot be efficiently integrated with professional collection software.
Agent types based on agent operation cycle

Static IP proxy: Stable and exclusive guarantee
In the scope of proxy services, static IP proxy is like an unshakable fortress, supporting a stable network world for users. When these proxy IPs are assigned to specific users, they are like the user's exclusive territory. Unless the user actively changes or the service provider updates it according to regulations, it will always be used by the user. Data center proxy service providers usually adopt this model to meet users' pursuit of stability and exclusivity by selling packages containing a fixed number of proxy IPs. Users can arrange the use of these IPs as they wish, whether it is automated operation with the help of robots or manual plug-in settings, they can enjoy the efficiency and convenience brought by exclusive agents. However, static IPs may also be blocked by target websites. In this case, service providers will change IPs in a timely manner to maintain uninterrupted user services.
For example, if a company needs to access a specific foreign website to obtain data in a long-term and stable manner, using a static IP proxy can ensure that the network environment for each visit is relatively stable, reducing the uncertainty caused by IP changes. ISP static residential IP proxy services have become the goal pursued by many companies and individuals with their excellent stability, high security and strong trust. BitBrowser analyzes this type of proxy in detail in this article. Click to learn more: (How to choose a good ISP proxy? Use BitBrowser Fingerprint Browser to protect account security).
Dynamic Rotation IP Proxy: Flexible and Changeable Network Camouflage
In comparison, the dynamic rotation IP proxy is more like a flexible and changeable dancer, jumping freely on the stage of the network. The notable feature of this type of proxy is its automatic rotation mechanism, that is, after a certain period of time or a certain number of requests, the currently used proxy IP will be automatically replaced with a new IP. This design not only greatly enhances the anonymity of users, but also cleverly avoids restrictions or bans that may be caused by frequent use of the same IP. For scenarios where large-scale data crawling is required, dynamic rotating IP proxies are undoubtedly the best choice. They are more common in residential proxy services, but in recent years, some data center proxy service providers have also begun to try to introduce this feature to meet users' dual desire for flexibility and security.
For example, when performing large-scale web crawling, dynamic rotating IP proxies can make crawlers less likely to be identified and blocked by target websites.
A new analysis of proxy types based on data processing logic
Forward proxy: a mysterious channel for anonymous access
Forward proxy, like a mysterious channel connecting users to the Internet, plays a key role in achieving anonymous access to web content. When a user accesses a website with the help of a forward proxy, the proxy server first receives the request sent by the user and passes it to the target web server. After the server completes the processing, the response result is fed back to the user through the proxy server. During this whole process, the user's real IP address is cleverly hidden, thus achieving the goal of anonymous access. In fact, many of the proxy types we have discussed before, such as static IP proxy and dynamic rotating IP proxy, can essentially be regarded as different manifestations of forward proxy.
For example, some users can use forward proxy to access specific online resources without regional restrictions.
Reverse proxy: a solid shield on the server side
Different from forward proxy, reverse proxy is more responsible for guarding the server side. It is at the front end of the Web server, responsible for processing various requests from the client, and forwarding, verifying or caching according to pre-set rules. Reverse proxy can not only significantly improve the security of Web servers, but also prevent them from being directly exposed.In the external network environment, load balancing technology can also be used to optimize server performance and improve user experience. Although reverse proxy is not directly used to achieve anonymous access, its value in protecting server resources and improving service efficiency cannot be underestimated.
For example, large e-commerce websites can effectively cope with high concurrent access through reverse proxy to ensure the stable operation of the server.
In-depth exploration of proxy types based on IP reuse strategy
Original proxy: a pure field that has not been involved
Original proxy, as the name suggests, refers to proxy IPs that have not been used to access specific websites. Although these IPs may not be completely new and unused, they have not been used for user-specified purposes before entering the user's package. Therefore, original proxy is of vital importance to maintain the novelty of access behavior and avoid triggering the website's blocking mechanism. Many proxy service providers will strictly control the scope of use of original proxy to ensure its purity and effectiveness.
For example, some financial data crawling businesses that have extremely high requirements for data freshness will give priority to original proxy.
Second-hand or resale proxy: an opportunity to revitalize
The corresponding to the original proxy is the second-hand or resale proxy. These proxy IPs may have been used in different scenarios and purposes in the past, but as time goes by and the website's ban policy is adjusted, they may have the opportunity to be used again. Through reasonable strategies and appropriate time arrangements, users can use these second-hand proxies to achieve efficient data crawling or access operations without violating the website's rules. Of course, this also requires users to have a certain level of risk judgment and strategic planning.
For example, some small startups, with limited budgets, may choose second-hand proxies to meet short-term business needs.
Is BitBrowser Finger Browser necessary when using proxy IPs?
As an advanced multi-account management tool, BitBrowser can create unique online identity simulation conditions for users. It gives each browser environment exclusive cookies, unique fingerprint features, and separate cache folders, etc.
From the perspective of the website, each such browser environment is like a completely independent user individual. This powerful fingerprint isolation technology is of great significance to users who need to control multiple accounts at the same time, especially when preventing accounts from being associated or even banned.
But it should be clear that relying solely on fingerprint isolation cannot fully guarantee the absolute security of accounts. IP address is another key identification mark of users in the Internet world. If multiple accounts log in through the same IP address, there is a high probability that these accounts will be associated with each other, which will greatly increase the risk of being blocked. Therefore, when you use fingerprint browsers, you must pay attention to the isolation of IP. Try to equip multiple accounts under the same platform with different IP addresses, whether static or dynamic.
Are you curious about how to get a proxy after seeing this? Don't worry, BitBrowser's partners provide you with a variety of proxies to meet your various business needs. You only need to download BitBrowser and get it through the proxy IP tab.
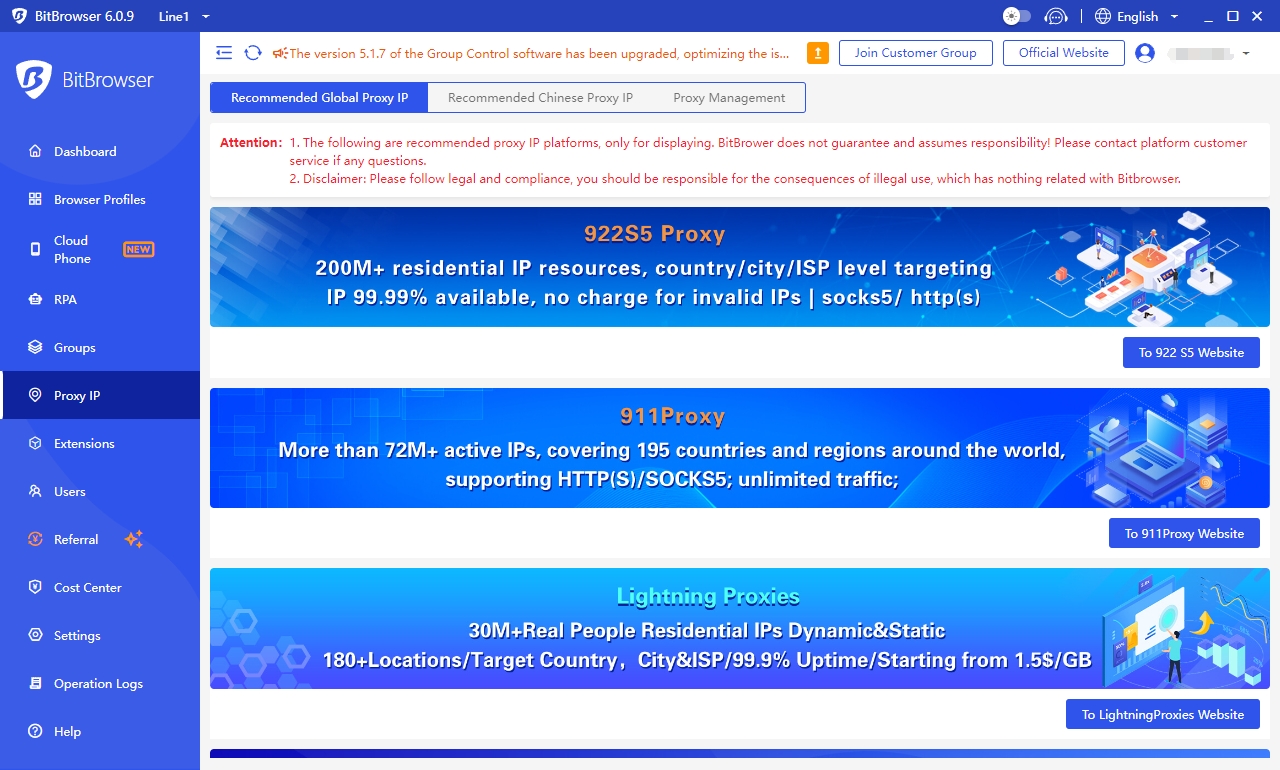
How to configure IP proxy in BitBrowser
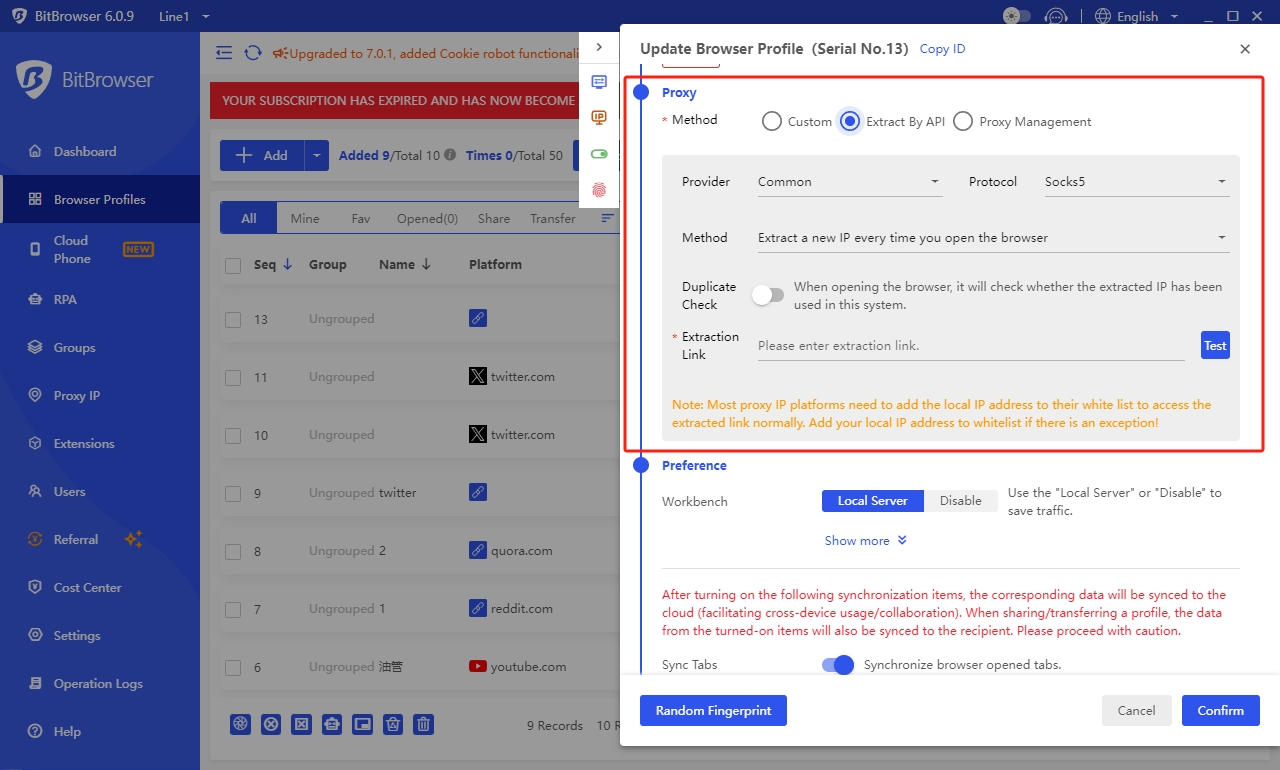
In BitBrowser, you can set a proxy IP for each browser environment to ensure that the same IP is used for each login, which is particularly important for accounts that require IP for operation.
Or, you can choose to enable IP and get a different IP address every time you open the browser. (The change mode of the proxy IP needs to be confirmed with the proxy service provider, and you need to select the IP according to your own business scenario).
When you create a browser environment in BitBrowser, in the [Proxy Configuration] column, first select the proxy type, then fill in the proxy host, port, proxy account, password and other related information. If you want to get more detailed settings, you can go to the BitBrowser Help Center.
Summary:
BitBrowser Fingerprint Browser and IP isolation strategy work together to provide e-commerce practitioners with a powerful tool. By accurately configuring static or dynamic IP in BitBrowser, users can significantly reduce account risks caused by IP problems. If you have had your account blocked due to multiple openings of Chrome browser before, then maybe you should try BitBrowser, an innovative anti-association browser. Now you can get 10 permanent free configuration files of this configuration file by downloading BitBrowser.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



