
Hot Picks
How to run Facebook ads in 2025? Ideas

Hot Picks
How to promote on Amazon? Sharing various promotion methods

Hot Picks
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn
Overseas social media matrix anti-association strategy: proxy IP unlimited browser
Time: 2024-07-27 10:57 Click:

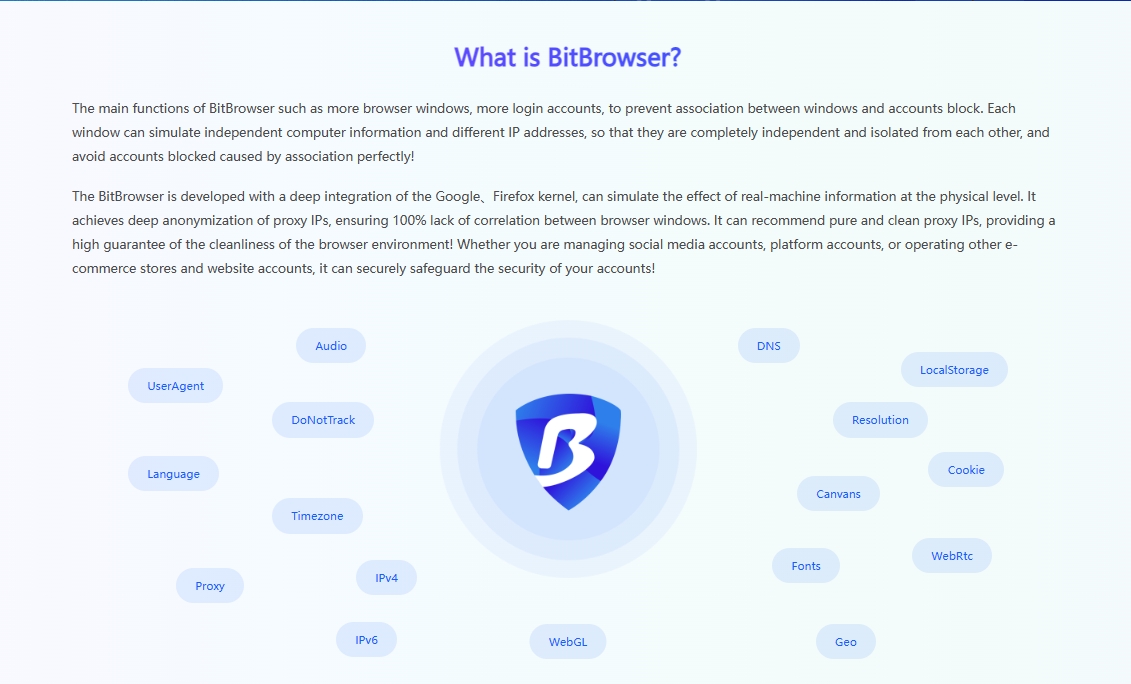
In this digital age filled with massive data, social media is not only a tool for people to communicate in daily life, but also an important platform for personal image building and business expansion. However, with the continuous development of social networks, the problem of account association is like a crisis lurking in the dark, silently eroding the privacy and security of users. Next, this article will lead you to deeply explore the root cause of the easy association of overseas social media matrices, and unveil the mystery and practical skills of proxy IP unlimited browser as a privacy defender.
1. Unveiling the mystery of overseas social media matrix association
The so-called social media account association, in simple terms, is that multiple different platforms connect and integrate many accounts of the same user through a series of clues, thereby weaving a huge personal information network. Behind this phenomenon, there are many factors that lead to its occurrence:
The interweaving of digital traces: similar interest identifiers, interaction forms and content preferences left by users on multiple platforms are like pieces of puzzles, which are pieced together one by one by sophisticated algorithms. For example, if a user frequently follows topics related to fitness, food, and travel on multiple social platforms, the platform's algorithm can easily infer that these accounts may belong to the same person through these common interests.
Device fingerprint identification and tracking: Even if you change accounts, if the device's hardware information (such as MAC address, browser fingerprint, etc.) has not changed, it can easily become a clue to association. For example, if you use multiple social media accounts on the same computer or mobile phone, even if you log in to a different account each time, the inherent characteristics of the device may still be recognized and associated by the platform.
Synchronous overlap of network behavior: The overlap of login time and IP address, especially when operating multiple accounts in the same network environment, is tantamount to actively exposing your identity to the platform. Imagine that you log in to multiple social accounts at the same time every day with the same IP address. This is a very obvious association signal for the platform's monitoring system.
Social graph mapping association: The overlap of friend relationships and follow lists constructs a complex social graph between users, further increasing the risk of association. Assuming that your multiple accounts follow the same group of friends or celebrities, the platform is likely to judge that these accounts are associated based on this.

2. Proxy IP Unlimited Browser Protects Your Security
Facing the severe challenges brought by account association, Proxy IP Unlimited Browser is like a sharp sword in the hands of users, building an indestructible protective barrier for users in the following ways:
Clever disguise of identity: By changing IP addresses, users can easily travel around the world, giving each account a unique "coat" to make it difficult for the platform to track its true identity. For example, you can use Proxy IP Unlimited Browser with Proxy IP to display your network location as the United States, and then switch to Japan, so that the platform cannot accurately determine your true source.
Geographic location simulation: Simulating IPs from different countries or regions not only breaks geographical restrictions, but also makes users' network activities elusive and mysterious. This means that you can access content that is restricted in specific regions, while also increasing the privacy of your account.
Flexible strategy for dynamic switching: Regularly or randomly changing proxy IPs increases the difficulty of platform identification, makes the behavior of the account appear more natural, and effectively reduces the possibility of being associated. For example, you can set it to automatically change the IP address every few hours or according to your frequency of use.
Isolation barrier for multiple accounts: Assign exclusive independent proxy IPs to different accounts to create an independent network environment and truly achieve complete isolation between accounts, just like creating an independent "room" for each account without interfering with each other.
Exclusively customized intimate service: Select high-quality, low-latency exclusive proxy services to ensure the security and stability of data transmission, while avoiding the potential risks that may be brought by shared proxies. Some professional proxy IP unlimited browsers can provide you with tailor-made browser fingerprint solutions based on your specific needs and customize the required browser fingerprints.

3. Proxy IP Unlimited Browser Usage Guidelines
Although the proxy IP unlimited browser provides strong support for social privacy protection, users still need to be vigilant during use and carefully avoid potential risks:
The first principle of compliance: Make sure that the use of proxy services complies with local laws and regulations and resolutely do not touch the red line of the law. In some countries and regions, the use of unauthorized proxy IPs may be suspected of being illegal. For example, in China, without the approval of the telecommunications authorities, it is not allowed to establish or rent dedicated lines (including virtual private networks VPN) and other channels to carry out cross-border activities.
Careful selection: Choose a proxy service provider with good reputation and mature technology to ensure the reliability and security of the service. There are many proxy IP unlimited browser services on the market, but the quality is uneven. Some bad providers may leak users' personal information or provide unstable services, resulting in poor network experience or even losses.
The supremacy of privacy protection: give priority to proxy services that promise not to record user data to minimize the risk of information leakage. Because once the proxy service provider records your access data, there is no guarantee that this information will not be abused or leaked.
Continuous monitoring and control: Regularly check the performance and stability of the proxy IP, and adjust the strategy in time to meet new challenges. For example, if you find that a proxy IP often has connection interruptions or slow speeds, you should replace it in time.
4, reasonable use of proxy IP with proxy IP unlimited browser
In order to better use the proxy IP unlimited browser to protect our privacy in the overseas social media matrix, we need to formulate a reasonable usage strategy. First, according to your needs and usage scenarios, choose the appropriate proxy with unlimited proxy IP browser type. For example, static proxy IP with unlimited IP browser is suitable for long-term stable needs, while dynamic proxy with unlimited proxy IP browser is more suitable for frequent changes.
Secondly, when setting up unlimited proxy IP browser, pay attention to the correctness of configuring IP proxy, including the address, port number, authentication information, etc. of the proxy server, to ensure successful connection and normal use.
In addition, other privacy protection measures should be combined, such as using strong passwords, updating passwords regularly, enabling two-factor authentication, etc., to form a comprehensive privacy protection system.
At the same time, keep an eye on the policies of social media platforms, because the platforms may constantly update their regulations on account association and proxy IP use. Violation of platform regulations may result in account bans or other restrictions.
With the continuous development of technology, social media platforms and regulators are also constantly improving and perfecting measures for account association and privacy protection. On the one hand, platforms may adopt more advanced algorithms and technologies to detect abnormal account behavior and proxy IP unlimited browser use; on the other hand, regulators will also strengthen supervision of network privacy and security.
In this context, we need to continuously improve our privacy protection awareness and skills to adapt to new changes and challenges. At the same time, we also look forward to more complete and reliable technologies and solutions in the future to provide users with stronger privacy protection in the digital social field.
Summary:
At a time when social media has gradually become an indispensable part of life, protecting personal privacy has become an important task that cannot be underestimated. The proxy IP unlimited browser has built a solid privacy defense line for users in the digital world with its unique advantages. However, true security still depends on the user's own caution and wise choices. Only by using proxy services reasonably and legally and matching the proxy IP unlimited browser can we gain a firm foothold in this battle of privacy protection and enjoy a freer and safer social experience. As a leader in the proxy IP unlimited browser, BitBrowser provides users with a convenient and safe anti-association experience. Download now and get 10 permanent free windows immediately.

 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management



